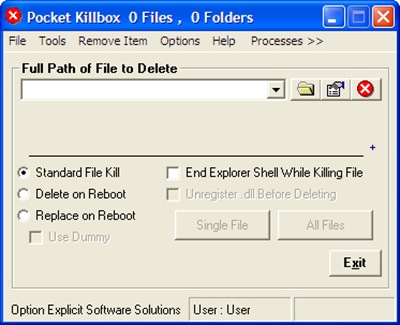
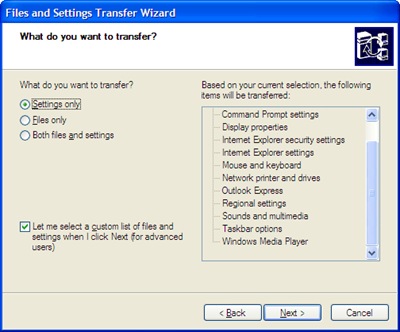
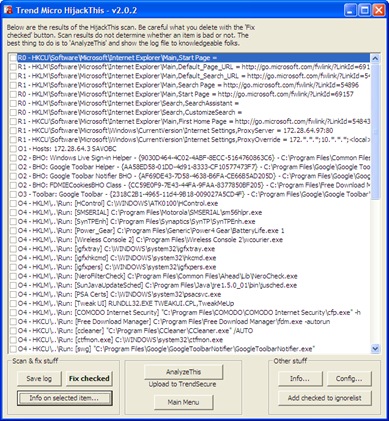
Pocket Killbox from Option^Explicit Software Solutions is a good Process & File Killer. The developer offers this nice utility as a freeware product and recommends: Use Killbox, When asking nicely doesn't work.
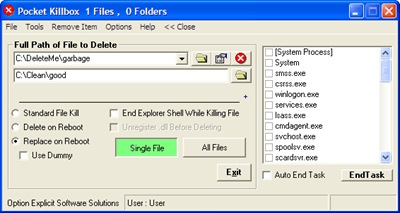
You can type full path of file/folder to delete or you can browse for its path by clicking ![]() button. Clicking
button. Clicking ![]() button shows properties of chosen file/folder, and
button shows properties of chosen file/folder, and ![]() button informs Killbox to delete selected file/folder. Killbox offers you following 3 options for removing the file/folder.
button informs Killbox to delete selected file/folder. Killbox offers you following 3 options for removing the file/folder.
- Standard File Kill
- Delete on Reboot
- Replace on Reboot
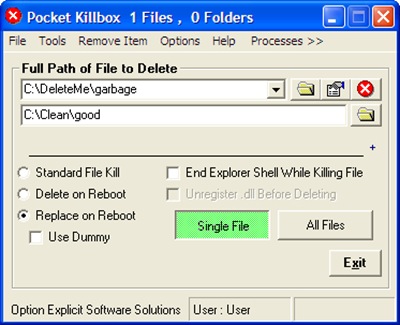
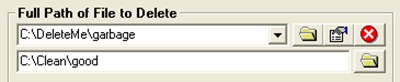
First 2 options are obvious; the 3rd option allows you to replace the selected file with a dummy file, if you don’t want to name the file replacing the file being deleted. In the following example, we want to replace C:\DeleteMe\garbage with C:\Clean\good file.
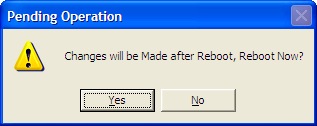
Clicking ![]() button inform you that changes will be made after reboot, and prompts you to reboot the computer.
button inform you that changes will be made after reboot, and prompts you to reboot the computer.
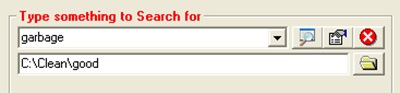
If you are unsure about file name and location, Killbox offers you file search also. Press Ctrl-F key sequence or click on Tools > File Find. Now type something to search and press Enter key or click on ![]() button.
button.
Killbox searches your computer hard disk and displays full path to the file/folder.
Before deleting file/folder, Killbox takes its backup in !KillBox folder in root of your hard disk.
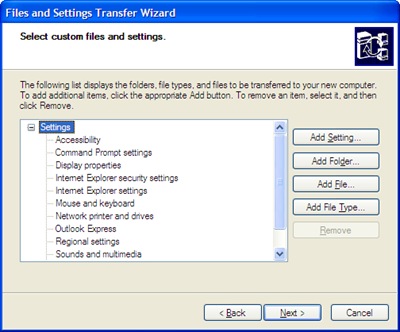
Following options offers more control over file/folder deletion process.
- End Explorer Shell While Killing File
- Unregister .dll before Deleting
If you choose to end Explorer Shell (explorer.exe), you can start the same by clicking on Tools > Start Explorer Shell.
The Tools menu has also few other useful items.
- Delete Temp Files
Allows you to delete temporary Internet files, temp files, cookies, Dr. Watson dumps, prefetch files, recent document list, history, Sun Java cache, etc. for user profiles found in the computer.
- Go to SessionManager
Launches Registry Editor and open HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager key
- Open Wininit.ini
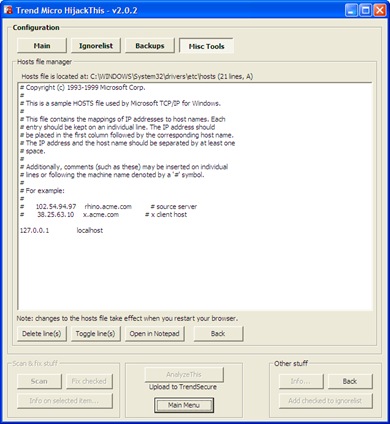
- Hosts file
Launches Notepad and opens %systemroot%\system32\drivers\etc\hosts file which contains mapping of IP addresses to corresponding host names
- Open Services
Launches Services applet, i.e., %SystemRoot%\system32\services.msc
- Open Wininit.ini
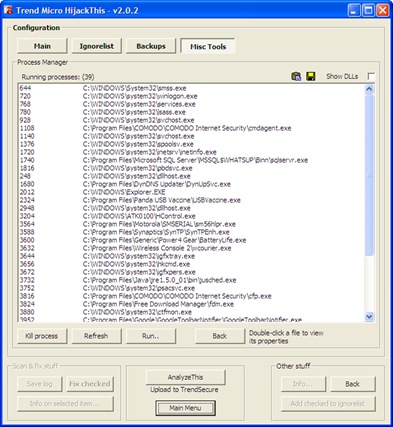
Clicking on Processes >> menu item expands Killbox GUI to show you list of running processes.
To end a running process, select checkbox before the executable name and click on End Task button.
Overall, Killbox is very useful in removing persistent file, and killing running processes.
_PNG.png)