HijackThis from Trend Micro is a free hijack detection tool that scans your Windows PC for Browser Helper Objects (BHOs), autorun programs, Windows Explorer context menu objects, hosts file etc. and generates a log file.
Scan results are displayed one line per entry.
Each entry is preceded with a checkbox and a group code. HijackThis v2.0.2 defines different sections of hijacking possibilities into following groups.
R - Registry, StartPage/SearchPage changes
R0 - Changed registry value
R1 - Created registry value
R2 - Created registry key
R3 - Created extra registry value where only one should be
F - IniFiles, autoloading entries
F0 - Changed inifile value
F1 - Created inifile value
F2 - Changed inifile value, mapped to Registry
F3 - Created inifile value, mapped to Registry
N - Netscape/Mozilla StartPage/SearchPage changes
N1 - Change in prefs.js of Netscape 4.x
N2 - Change in prefs.js of Netscape 6
N3 - Change in prefs.js of Netscape 7
N4 - Change in prefs.js of Mozilla
O - Other, several sections which represent:
O1 - Hijack of auto.search.msn.com with Hosts file
O2 - Enumeration of existing MSIE BHO's
O3 - Enumeration of existing MSIE toolbars
O4 - Enumeration of suspicious autoloading Registry entries
O5 - Blocking of loading Internet Options in Control Panel
O6 - Disabling of 'Internet Options' Main tab with Policies
O7 - Disabling of Regedit with Policies
O8 - Extra MSIE context menu items
O9 - Extra 'Tools' menuitems and buttons
O10 - Breaking of Internet access by New.Net or WebHancer
O11 - Extra options in MSIE 'Advanced' settings tab
O12 - MSIE plugins for file extensions or MIME types
O13 - Hijack of default URL prefixes
O14 - Changing of IERESET.INF
O15 - Trusted Zone Autoadd
O16 - Download Program Files item
O17 - Domain hijack
O18 - Enumeration of existing protocols and filters
O19 - User stylesheet hijack
O20 - AppInit_DLLs autorun Registry value, Winlogon Notify Registry keys
O21 - ShellServiceObjectDelayLoad (SSODL) autorun Registry key
O22 - SharedTaskScheduler autorun Registry key
O23 - Enumeration of NT Services
O24 - Enumeration of ActiveX Desktop Components
Detailed information about an entry can be obtained by selecting it from the list of found items or highlighting the relevant line, and clicking Info on selected item. You can select an entry and click on Fix checked button. Though HijackThis backups any changes made to the system and allows you to restore backup in case the things don’t work it is still advisable that before fixing any entry, make sure that you have taken backup of Windows registry. You can see the backups created by HijackThis by clicking the View the list of backups button in Main menu.
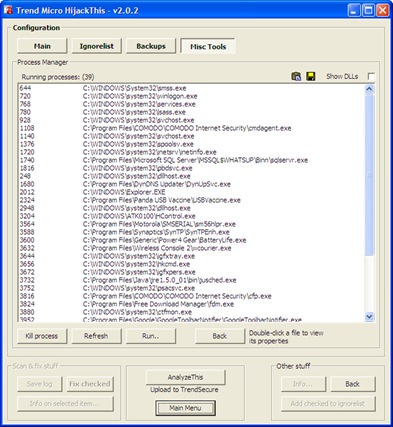
Apart from scanning of several kinds of hijacking possibilities, HijackThis also offers some useful tools. To access these tools click the Open the Misc Tools section button in Main menu.
There are following 6 useful tools:
- Process manager
- Hosts file manager
- Tool to delete a file on reboot
- Tools to delete an NT service
- Tool to scan for alternate data stream
- Uninstall manager
The Process manager lists all running process with their Process Identifier (PID) and full path to the corresponding file.
The hosts file which contains mapping of IP addresses to host names, is located in %systemroot%\system32\drivers\etc folder in Windows XP. The Hosts file manager open the hosts file and allows you to delete IP address mapping or open hosts file for editing in Notepad.
Uninstall manager extends functionality of standard Add or Remove Program Control Panel applet. You can delete/edit uninstall entries, however restoration of deleted entry is not possible.






_PNG.png)
No comments:
Post a Comment