Comodo Internet Security (CIS) from Comodo Security Solutions Inc. provides complete threat protection by combining
- A powerful antivirus software that automatically detects and eliminates viruses, Worms and Trojan horses;
- An enterprise class packet filtering firewall that constantly defends your computer from inbound and outbound internet attacks; and
- A rule-based intrusion prevention system called Defense+ that protects your critical operating system files from malicious processes, internal attacks and blocks unknown malware.
Let’s download a copy of CIS setup from http://personalfirewall.comodo.com/download_firewall.html and start CIS installation.
Click on OK button.
Click on Next button.
Go through the License Agreement and click on I accept button.
Choose the destination folder and click on Next button.
Enter your email address to receive product updates, PC security tips, and click on Next button.
Check on Install COMODO Antivirus, Install COMODO Firewall and click on Next button.
Choose your option to join or skip ThreatCast community, and click on Next button.
Check on Install COMODO Hopsurf Toolbar, if you want to integrate the COMODO recommended way to protect your favourite browser. Click on Next button.
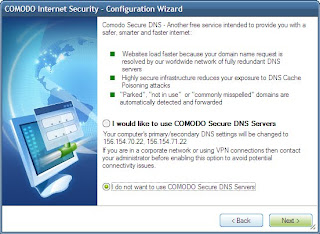
COMODO Secure DNS is another recommended service that is provided free of cost. Click on Next button.
Click on Finish button to allow CIS setup activate product license.
Click on Finish button to restart the computer. After restarting the computer, CIS detects a new private network.
You may assign a name to this network. However, the CIS assigned name is OK. Click on OK button.
Open COMODO Internet Security Start menu subgroup and launch COMODO Internet Security.
CIS has a nice and user-friendly interface to work with. We have not updated the virus signature database, yet. But before that have a look at the functionality of the CIS. Click on the ANTIVIRUS button in top command bar.
Click on Scanner Settings button.
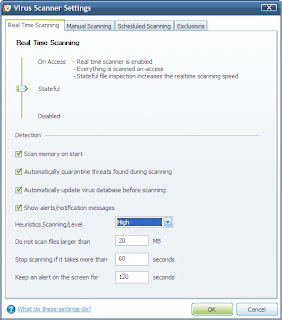
Set options for Real Time Scanning and click on Manual Scanning tab.
Set options for Manual Scanning and click on Scheduled Scanning tab.
Click on Stealth Ports Wizard button. The wizard is used to create invisible ports for your network. You have 3 options to define stealth ports. You can define new trusted network, you can set CIS to alert you for every incoming connection on per-case basis or you can block all incoming connection to your computer.
Suppose we want to define trusted network. Click on Next button.
By default there are no blocked network zones. You may add network zones, with which you want to avoid any packet interchange. Click on Cancel button. Click on DEFENSE+ button to see interface for host intrusion prevention system module.
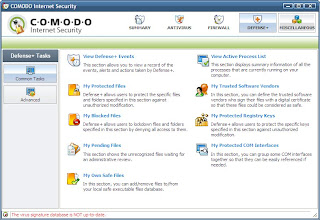
Click on View Active Process List button.
This shows all processes running in your system with their hierarchy in process tree, process identifier, module developer's name, and user account name. Click on Close button. Then click on My Trusted Software Vendors button.
Click on Cancel button. Then click on My Protected Registry Keys button.
This displays all Windows Registry keys protected by CIS. You can add/edit/remove/group registry keys for better protection to suit your security requirements. Likewise clicking on My Protected COM Interfaces shows you which COM (Component Object Model) interfaces have been secured by CIS.
This was a general walkthrough of Comodo Internet Security installation and features. CIS is an industrial grade security product delivered free of cost. Highly recommended to be installed on your Windows PC.
Open COMODO Internet Security Start menu subgroup and launch COMODO Internet Security.
CIS has a nice and user-friendly interface to work with. We have not updated the virus signature database, yet. But before that have a look at the functionality of the CIS. Click on the ANTIVIRUS button in top command bar.
Click on Scanner Settings button.

Set options for Real Time Scanning and click on Manual Scanning tab.
Set options for Manual Scanning and click on Scheduled Scanning tab.
Set options for Scheduled Scanning and click on Exclusions tab.
Click on OK button to close Virus Scanner Settings window. Click on FIREWALL button.
Click on Stealth Ports Wizard button. The wizard is used to create invisible ports for your network. You have 3 options to define stealth ports. You can define new trusted network, you can set CIS to alert you for every incoming connection on per-case basis or you can block all incoming connection to your computer.
Suppose we want to define trusted network. Click on Next button.
Select you network zone and click on Finish button.
Click on OK button. Now click on View Active Connections button. The Active Connections interface contains summary of all currently active connections on a per-application basis. This list is updated in real time whenever an application creates a new connection or drops an existing connection. You can view all the connected applications, source, destination, and total amount of traffic that has passed in and out of your system over each connection.
Click on Close button. Click on My Port Sets button. A number of standard ports are listed on functionality basis. You can add your application ports, edit or remove existing ports.
Once you are done defining your set of ports, click on Apply button. Click on My Network Zones button.
Click on Apply button to go back to Firewall management interface. Click on My Blocked Network Zones button.
By default there are no blocked network zones. You may add network zones, with which you want to avoid any packet interchange. Click on Cancel button. Click on DEFENSE+ button to see interface for host intrusion prevention system module.

Click on View Active Process List button.
Click on Cancel button. Then click on My Protected Registry Keys button.
This displays all Windows Registry keys protected by CIS. You can add/edit/remove/group registry keys for better protection to suit your security requirements. Likewise clicking on My Protected COM Interfaces shows you which COM (Component Object Model) interfaces have been secured by CIS.
This was a general walkthrough of Comodo Internet Security installation and features. CIS is an industrial grade security product delivered free of cost. Highly recommended to be installed on your Windows PC.




























_PNG.png)
No comments:
Post a Comment